安全、可靠、值得信赖的内存计算加速器
IF 33.7
1区 工程技术
Q1 ENGINEERING, ELECTRICAL & ELECTRONIC
引用次数: 0
摘要
基于新兴内存设备的内存计算(CIM)加速器因其强大的功能和性能,在边缘人工智能和机器学习应用中具有潜在用途。然而,在广泛部署之前,需要确保 CIM 加速器的隐私和安全性。在此,我们将探讨如何开发安全可靠的 CIM 加速器。我们将研究 CIM 加速器特有的漏洞,以及减轻这些威胁(包括对抗性攻击和侧信道攻击)的策略。然后,我们利用内存设备的固有随机性讨论了 CIM 系统的安全机遇。最后,我们考虑将安全因素纳入未来 CIM 加速器的设计中,以实现安全和保护隐私的边缘人工智能应用。本文章由计算机程序翻译,如有差异,请以英文原文为准。
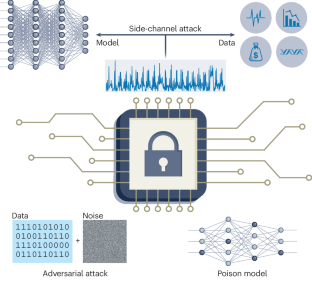

Safe, secure and trustworthy compute-in-memory accelerators
Compute-in-memory (CIM) accelerators based on emerging memory devices are of potential use in edge artificial intelligence and machine learning applications due to their power and performance capabilities. However, the privacy and security of CIM accelerators needs to be ensured before their widespread deployment. Here we explore the development of safe, secure and trustworthy CIM accelerators. We examine vulnerabilities specific to CIM accelerators, along with strategies to mitigate these threats including adversarial and side-channel attacks. We then discuss the security opportunities of CIM systems, leveraging the intrinsic randomness of the memory devices. Finally, we consider the incorporation of security considerations into the design of future CIM accelerators for secure and privacy-preserving edge AI applications. This Perspective examines the development of safe, secure and trustworthy compute-in-memory accelerators, exploring vulnerabilities specific to such accelerators and discussing the security opportunities of the systems.
求助全文
通过发布文献求助,成功后即可免费获取论文全文。
去求助
来源期刊
Nature Electronics
Engineering-Electrical and Electronic Engineering
CiteScore
47.50
自引率
2.30%
发文量
159
期刊介绍:
Nature Electronics is a comprehensive journal that publishes both fundamental and applied research in the field of electronics. It encompasses a wide range of topics, including the study of new phenomena and devices, the design and construction of electronic circuits, and the practical applications of electronics. In addition, the journal explores the commercial and industrial aspects of electronics research.
The primary focus of Nature Electronics is on the development of technology and its potential impact on society. The journal incorporates the contributions of scientists, engineers, and industry professionals, offering a platform for their research findings. Moreover, Nature Electronics provides insightful commentary, thorough reviews, and analysis of the key issues that shape the field, as well as the technologies that are reshaping society.
Like all journals within the prestigious Nature brand, Nature Electronics upholds the highest standards of quality. It maintains a dedicated team of professional editors and follows a fair and rigorous peer-review process. The journal also ensures impeccable copy-editing and production, enabling swift publication. Additionally, Nature Electronics prides itself on its editorial independence, ensuring unbiased and impartial reporting.
In summary, Nature Electronics is a leading journal that publishes cutting-edge research in electronics. With its multidisciplinary approach and commitment to excellence, the journal serves as a valuable resource for scientists, engineers, and industry professionals seeking to stay at the forefront of advancements in the field.
 求助内容:
求助内容: 应助结果提醒方式:
应助结果提醒方式:


