自动驾驶多传感器融合定位安全分析及自适应假数据注入
IF 15.5
1区 计算机科学
Q1 COMPUTER SCIENCE, ARTIFICIAL INTELLIGENCE
引用次数: 0
摘要
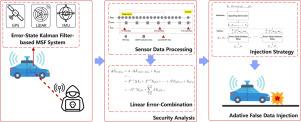
多传感器融合(MSF)算法是现代自动驾驶系统的关键组成部分,特别是在定位和人工智能感知模块中,对确保车辆安全起着至关重要的作用。错误状态卡尔曼滤波器(ESKF)作为一种专门用于定位融合的算法,以其鲁棒性和准确性得到了广泛的认可。虽然现有的研究已经证明了ESKF对传感器欺骗攻击的脆弱性,但这些工作主要集中在黑盒实现上,导致安全性分析不足。具体来说,由于以前的方法缺乏理论指导,这些研究一直依赖于指数函数来拟合所有场景的攻击序列。因此,攻击者必须探索广泛的参数空间来识别有效的攻击序列,而缺乏自适应生成最优攻击序列的能力。本文旨在通过对ESKF模型进行彻底的安全性分析,并提出一种简单的方法来对这些系统中的注入错误进行建模,从而填补这一关键空白。利用这种误差建模,我们引入了一种新的攻击策略,该策略采用约束优化来减少达到相同偏差目标所需的能量,保证了攻击的高效和有效。这种方法增加了攻击的隐蔽性,使其更难被发现。与以前的方法不同,我们的方法可以动态生成近乎完美的注入信号,而无需在不同场景中多次尝试寻找最佳参数组合。通过广泛的模拟和真实世界的实验,我们证明了与最先进的攻击策略相比,我们的方法具有优越性。我们的研究结果表明,我们的方法需要更少的注入能量来达到相同的偏差目标。此外,我们还通过在人工智能驱动的自动驾驶系统上进行端到端测试,验证了我们方法的实用性和影响。本文章由计算机程序翻译,如有差异,请以英文原文为准。
Security analysis and adaptive false data injection against multi-sensor fusion localization for autonomous driving
Multi-sensor Fusion (MSF) algorithms are critical components in modern autonomous driving systems, particularly in localization and AI-powered perception modules, which play a vital role in ensuring vehicle safety. The Error-State Kalman Filter (ESKF), specifically employed for localization fusion, is widely recognized for its robustness and accuracy in MSF implementations. While existing studies have demonstrated the vulnerability of ESKF to sensor spoofing attacks, these works have primarily focused on a black-box implementation, leading to an insufficient security analysis. Specifically, due to the lack of theoretical guidance in previous methods, these studies have consistently relied on exponential functions to fit attack sequences across all scenarios. As a result, the attacker had to explore an extensive parameter space to identify effective attack sequences, lacking the ability to adaptively generate optimal ones. This paper aims to fill this crucial gap by conducting a thorough security analysis of the ESKF model and presenting a simple approach for modeling injection errors in these systems. By utilizing this error modeling, we introduce a new attack strategy that employs constrained optimization to reduce the energy needed to reach the same deviation target, guaranteeing that the attack is both efficient and effective. This method increases the stealthiness of the attack, making it harder to detect. Unlike previous methods, our approach can dynamically produce nearly perfect injection signals without requiring multiple attempts to find the best parameter combination in different scenarios. Through extensive simulations and real-world experiments, we demonstrate the superiority of our method compared to state-of-the-art attack strategies. Our results indicate that our approach requires significantly less injection energy to achieve the same deviation target. Additionally, we validate the practical applicability and impact of our method through end-to-end testing on an AI-powered autonomous driving system.
求助全文
通过发布文献求助,成功后即可免费获取论文全文。
去求助
来源期刊

Information Fusion
工程技术-计算机:理论方法
CiteScore
33.20
自引率
4.30%
发文量
161
审稿时长
7.9 months
期刊介绍:
Information Fusion serves as a central platform for showcasing advancements in multi-sensor, multi-source, multi-process information fusion, fostering collaboration among diverse disciplines driving its progress. It is the leading outlet for sharing research and development in this field, focusing on architectures, algorithms, and applications. Papers dealing with fundamental theoretical analyses as well as those demonstrating their application to real-world problems will be welcome.
 求助内容:
求助内容: 应助结果提醒方式:
应助结果提醒方式:


