DT-BFL: Digital Twins for Blockchain-enabled Federated Learning in Internet of Things networks
IF 4.8
3区 计算机科学
Q1 COMPUTER SCIENCE, INFORMATION SYSTEMS
引用次数: 0
Abstract
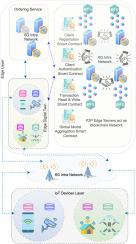
Sixth-generation (6G) wireless networks enable faster, smarter, and more connected Internet of Things (IoT) systems, which in turn support edge intelligence and real-time decision-making. Federated learning (FL) supports this shift by allowing devices to collaboratively train models without sharing raw data, which helps to protect user privacy. There are, however, potential security challenges in FL deployments. For example, security challenges such as poisoning attacks and Byzantine clients can compromise the training process and degrade the accuracy and reliability of the global model. Although existing methods can detect malicious updates, many advanced attacks still bypass statistical defenses relying on metrics such as median and distance. In other words, developing an FL system that ensures both reliable decision-making and privacy and security guarantees in IoT networks remains a significant challenge. This study introduces a Digital Twin-driven Blockchain-enabled Federated Learning (DT-BFL) framework designed for IoT networks. The framework creates a digital representation of the IoT environment to support secure and decentralized edge intelligence using blockchain and federated learning technologies. DT-BFL is built to detect and filter out potentially poisoned model updates from malicious participants. This is achieved through a new smart contract-enabled decentralized aggregation method called Local Updates Purify (LUP). LUP uses a two-stage filtering process: First, it applies Median Absolute Deviation (MAD) to initially remove outliers, then uses statistical features and clustering to separate honest from malicious updates before aggregating the global model. It also assigns a Trust Score (TS) to each participant based on how much their updates differ from the global model and then uses a genuine criterion to select honest clients by evaluating trust scores, update similarity, and deviation from the global model. Experimental results show that DT-BFL effectively defends against various poisoning attacks on datasets like MNIST, ToN-IoT, and CIFAR-10 using models such as CNN, MLP, ResNet, and DenseNet, and maintains high accuracy even when 50% of the clients are malicious. Using a permissioned blockchain further secures the system by enabling aggregation of the decentralized model and authentication of clients through smart contracts. The source code is available on https://github.com/UNSW-Canberra-2023/LUP.
DT-BFL:物联网网络中支持区块链的联邦学习的数字双胞胎
第六代(6G)无线网络使更快、更智能、更互联的物联网(IoT)系统成为可能,从而支持边缘智能和实时决策。联邦学习(FL)支持这种转变,它允许设备在不共享原始数据的情况下协作训练模型,这有助于保护用户隐私。然而,在FL部署中存在潜在的安全挑战。例如,诸如中毒攻击和拜占庭客户机之类的安全挑战可能危及训练过程,并降低全局模型的准确性和可靠性。尽管现有的方法可以检测到恶意更新,但许多高级攻击仍然绕过依赖于中位数和距离等指标的统计防御。换句话说,在物联网网络中开发一个既能确保可靠决策又能保证隐私和安全的FL系统仍然是一个重大挑战。本研究介绍了为物联网网络设计的数字双驱动区块链联邦学习(DT-BFL)框架。该框架创建了物联网环境的数字表示,以支持使用区块链和联邦学习技术的安全和分散的边缘智能。DT-BFL用于检测和过滤来自恶意参与者的潜在有毒模型更新。这是通过一种名为Local Updates Purify (LUP)的新的智能合约分散聚合方法实现的。LUP使用两阶段过滤过程:首先,它应用中位数绝对偏差(MAD)初始去除异常值,然后在聚合全局模型之前使用统计特征和聚类来分离诚实更新和恶意更新。它还根据每个参与者的更新与全局模型的差异程度为其分配信任分数(TS),然后使用真实标准通过评估信任分数、更新相似性和与全局模型的偏差来选择诚实的客户。实验结果表明,使用CNN、MLP、ResNet、DenseNet等模型,DT-BFL可以有效防御MNIST、ToN-IoT、CIFAR-10等数据集的各种中毒攻击,即使50%的客户端是恶意的,也能保持较高的准确率。使用允许的区块链通过智能合约支持分散模型的聚合和客户端身份验证,从而进一步保护系统。源代码可在https://github.com/UNSW-Canberra-2023/LUP上获得。
本文章由计算机程序翻译,如有差异,请以英文原文为准。
求助全文
约1分钟内获得全文
求助全文
来源期刊

Ad Hoc Networks
工程技术-电信学
CiteScore
10.20
自引率
4.20%
发文量
131
审稿时长
4.8 months
期刊介绍:
The Ad Hoc Networks is an international and archival journal providing a publication vehicle for complete coverage of all topics of interest to those involved in ad hoc and sensor networking areas. The Ad Hoc Networks considers original, high quality and unpublished contributions addressing all aspects of ad hoc and sensor networks. Specific areas of interest include, but are not limited to:
Mobile and Wireless Ad Hoc Networks
Sensor Networks
Wireless Local and Personal Area Networks
Home Networks
Ad Hoc Networks of Autonomous Intelligent Systems
Novel Architectures for Ad Hoc and Sensor Networks
Self-organizing Network Architectures and Protocols
Transport Layer Protocols
Routing protocols (unicast, multicast, geocast, etc.)
Media Access Control Techniques
Error Control Schemes
Power-Aware, Low-Power and Energy-Efficient Designs
Synchronization and Scheduling Issues
Mobility Management
Mobility-Tolerant Communication Protocols
Location Tracking and Location-based Services
Resource and Information Management
Security and Fault-Tolerance Issues
Hardware and Software Platforms, Systems, and Testbeds
Experimental and Prototype Results
Quality-of-Service Issues
Cross-Layer Interactions
Scalability Issues
Performance Analysis and Simulation of Protocols.
 求助内容:
求助内容: 应助结果提醒方式:
应助结果提醒方式:


