welch-gong流密码演化路径
IF 1.1
3区 计算机科学
Q3 COMPUTER SCIENCE, THEORY & METHODS
Cryptography and Communications-Discrete-Structures Boolean Functions and Sequences
Pub Date : 2023-08-05
DOI:10.1007/s12095-023-00656-0
引用次数: 2
摘要
本文章由计算机程序翻译,如有差异,请以英文原文为准。
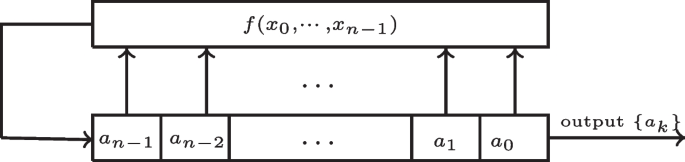
The welch-gong stream cipher - evolutionary path
求助全文
通过发布文献求助,成功后即可免费获取论文全文。
去求助
来源期刊

Cryptography and Communications-Discrete-Structures Boolean Functions and Sequences
COMPUTER SCIENCE, THEORY & METHODS-MATHEMATICS, APPLIED
CiteScore
2.50
自引率
7.10%
发文量
66
期刊介绍:
The scope of the journal focuses on discrete structures used in stream and block ciphers in symmetric cryptography; code division multiple access in communications; and random number generation for statistics, cryptography and numerical methods. In particular, papers covering Boolean functions and sequences, without excluding any other discrete structure used in cryptography and communications, such as finite fields and other algebraic structures, are strongly encouraged.
 求助内容:
求助内容: 应助结果提醒方式:
应助结果提醒方式:


