具有后量子加密和雾计算的可证明轻量级和安全的IoHT方案:医疗保健系统的综合方案
IF 1.9
Q2 MULTIDISCIPLINARY SCIENCES
引用次数: 0
摘要
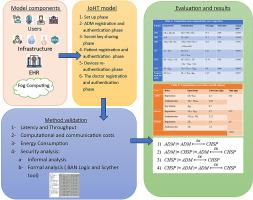
量子计算机对RSA (Rivest-Shamir-Adleman)和ECC (Elliptic Curve Cryptography)等常用公钥密码系统的安全性构成威胁。这是因为这些量子计算机有效地解决了因数分解和离散对数问题,这是RSA和ECC的基础。这损害了部署在各种应用程序(如医疗保健物联网(IoHT))中的安全系统的机密性、完整性和真实性。后量子加密虽然是一种潜在的解决方案,但它带来的计算开销可能会减慢服务的交付速度。这在IoHT安全关键系统中引起了严重的关注,因为它直接影响患者安全和医疗保健系统。本文旨在设计一种后量子电阻方案。我们的方案基于ECC、计数器模式(CTR)和密钥封装机制(KEM)。为了保证网络实体电子记录的安全和存储,并支持可扩展性,采用了区块链和星际文件系统(IPFS)。为了在访问特定数据和资源时实现更高级别的安全性和更有效的控制,我们应用了基于角色的访问控制(RBAC)。此外,我们还部署了对称可搜索加密(SSE),以实现高效和安全的数据搜索。该方案的安全性使用Scyther工具和Burrows-Abadi-Needham (BAN)逻辑进行了正式验证。此外,非正式的安全分析表明,我们提出的方案提供了相互认证、机密性、完整性和其他安全需求。此外,它还可以抵御众所周知的威胁和一些最近的威胁,如网络钓鱼、量子攻击和51%攻击。此外,还与其他相关协议进行了比较分析,以证明该方案在IoHT环境下的有效性。结果表明,该算法的计算开销减少了90%,通信开销和延迟也相对较低。另一方面,吞吐量大大提高,而能耗很低。该方案是一种低复杂度的IoHT环境解决方案,可解决现有威胁并保持数据完整性。区块链和IPFS确保网络实体的安全、可扩展的电子记录存储。通过RBAC实现安全、有效的访问控制,并通过SSE增强数据可搜索性。本文章由计算机程序翻译,如有差异,请以英文原文为准。
Provably lightweight and secure IoHT scheme with post-quantum cryptography and fog computing: A comprehensive scheme for healthcare system
Quantum computers threaten the security of commonly used public-key cryptosystems, such as Rivest-Shamir-Adleman (RSA) and Elliptic Curve Cryptography (ECC). This is because these quantum computers efficiently solve factorization and discrete logarithm problems, which are the basis for RSA and ECC. This compromises confidentiality, integrity, and authenticity in security systems deployed in various applications, such as Internet-of-Healthcare Things (IoHT). Post-quantum cryptography, while a potential solution, introduces computational overheads that can slow service delivery. This poses serious concerns in IoHT safety critical systems as it directly impacts patient safety and healthcare systems. This paper aims to design a post-quantum resistance scheme for IoHTs. Our scheme is based on ECC, Counter mode (CTR), and Key Encapsulation Mechanism (KEM). To guarantee the safety and storage of electronic records for the network entities and support scalability, blockchain and InterPlanetary File System (IPFS) were employed. To achieve improved levels of security and more effective control when accessing specific data and resources, we apply Role-Based Access Control (RBAC). In addition, we deploy Symmetric Searchable Encryption (SSE) for efficient and secure data search. The scheme's security was formally verified using the Scyther tool, and Burrows–Abadi–Needham (BAN) logic. In addition, informal security analysis shows that our proposed scheme offers mutual authentication, confidentiality, integrity, and other security requirements. In addition, it withstands well-known threats and some of the recent threats, such as phishing, quantum, and 51% attacks. Moreover, a comparative analysis was conducted with other related protocols to show the efficiency of the proposed scheme in the IoHT environment. The results indicate that the computation overhead was reduced by 90%, while communication cost and latency were relatively low. On the other hand, throughput was greatly increased while energy consumption was very low.
The proposed scheme is a low complexity solution for IoHT environments to address existing threats and maintain data integrity.
Blockchain and IPFS ensure secure, scalable e-record storage for network entities.
Achieving secure, effective access control with RBAC and enhancing data searchability with SSE.
求助全文
通过发布文献求助,成功后即可免费获取论文全文。
去求助
来源期刊

MethodsX
Health Professions-Medical Laboratory Technology
CiteScore
3.60
自引率
5.30%
发文量
314
审稿时长
7 weeks
期刊介绍:
 求助内容:
求助内容: 应助结果提醒方式:
应助结果提醒方式:


