AUKA:基于边缘的移动人群传感的异步可更新密钥协议
IF 3.7
2区 计算机科学
Q2 COMPUTER SCIENCE, INFORMATION SYSTEMS
Journal of Information Security and Applications
Pub Date : 2025-08-27
DOI:10.1016/j.jisa.2025.104213
引用次数: 0
摘要
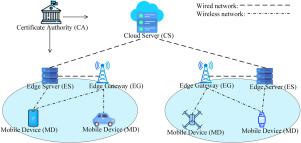
基于边缘的移动人群传感(E-MCS)通过利用边缘服务器进行本地任务处理、减少云负载和延迟来提高效率。然而,在移动设备和边缘服务器之间建立安全、低延迟的通信仍然是一个挑战。现有的密钥协议(KA)方案要么需要多轮交互,增加延迟和能耗,要么损害安全属性,如完美的前向安全性和密钥妥协模拟抗性。为了解决这些限制,我们提出了一种针对E-MCS量身定制的异步可更新KA (AUKA)方案。AUKA建立在密钥协议的基础上,结合了可更新密钥加密的设计概念,并利用哈希函数等标准加密原语来构建具有会话密钥更新机制的高效方案。AUKA实现了强大完善的前向安全性,即使移动设备的私钥和随机数被泄露,所有之前建立的会话密钥仍然是安全的,有效地降低了长期的安全风险。此外,AUKA维护一个几乎0-RTT的属性,支持有效的会话密钥建立和密钥更新,而不会引入过多的通信开销。在间隙计算Diffie-Hellman假设下证明了其安全性,并通过仿真验证了其有效性。结果表明,AUKA为E-MCS提供了高度安全和可扩展的解决方案。本文章由计算机程序翻译,如有差异,请以英文原文为准。
AUKA: Asynchronous updatable key agreement for edge-based mobile crowd sensing
Edge-based mobile crowd sensing (E-MCS) enhances efficiency by leveraging edge servers for local task processing, reducing cloud load and latency. However, establishing secure, low-latency communication between mobile devices and edge servers remains a challenge. Existing key agreement (KA) schemes either require multiple interaction rounds, increasing latency and energy consumption, or compromise security properties like perfect forward security and key-compromise impersonation resistance. To address these limitations, we propose an asynchronous updatable KA (AUKA) scheme tailored for E-MCS. AUKA is built upon key agreement, incorporating the design concept of updatable key encryption and leveraging standard cryptographic primitives such as hash functions to construct an efficient scheme with a session key update mechanism. AUKA achieves strong perfect forward security, even if a mobile device’s private key and random number are compromised, all previously established session keys remain secure, effectively mitigating long-term security risks. Additionally, AUKA maintains an almost 0-RTT property, enabling efficient session key establishment and key updates without introducing excessive communication overhead. We prove its security under the gap computational Diffie–Hellman assumption and validate its efficiency through simulations. Results demonstrate that AUKA offers a highly secure and scalable solution for E-MCS.
求助全文
通过发布文献求助,成功后即可免费获取论文全文。
去求助
来源期刊

Journal of Information Security and Applications
Computer Science-Computer Networks and Communications
CiteScore
10.90
自引率
5.40%
发文量
206
审稿时长
56 days
期刊介绍:
Journal of Information Security and Applications (JISA) focuses on the original research and practice-driven applications with relevance to information security and applications. JISA provides a common linkage between a vibrant scientific and research community and industry professionals by offering a clear view on modern problems and challenges in information security, as well as identifying promising scientific and "best-practice" solutions. JISA issues offer a balance between original research work and innovative industrial approaches by internationally renowned information security experts and researchers.
 求助内容:
求助内容: 应助结果提醒方式:
应助结果提醒方式:


