面向边缘设备恶意流量检测的网络流量轻量级表示学习
IF 3.7
2区 计算机科学
Q2 COMPUTER SCIENCE, INFORMATION SYSTEMS
Journal of Information Security and Applications
Pub Date : 2025-08-11
DOI:10.1016/j.jisa.2025.104186
引用次数: 0
摘要
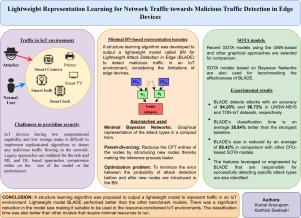
随着物联网(IoT)环境中连接设备数量的快速增加,其面临的威胁也显著增加。由于计算设施的易用性,攻击者可以更频繁地对这些网络发动复杂的攻击。物联网网络中的设备具有有限的计算能力,存储容量和硬件能力,因此使用传统方法保护它们具有挑战性。多年来,人们提出了许多基于机器学习和深度学习的方法来对流经边缘设备的流量进行分类,但这些模型有其局限性,例如由于这些设备的计算能力有限,对攻击的检测速度较慢,从而使得重参数模型无法在此类设备上运行。为了克服这一点,我们提出了一种结构学习算法来创建一个模型,该模型的结构学习是使用相关分析和PCA完成的,然后使用父母离婚和顺序最小二乘规划进行优化,从而创建一个模型,尽管在参数数量方面很精简,但仍表现出高性能。所选择的特征与每个攻击的相关性也通过定性映射和领域逻辑进行验证。使用UNSW-NB15和TON-IoT数据集对生成的模型进行了评估,在对恶意流量进行分类方面优于几种最先进的模型,特别是在推理时间和模型大小方面。尽管它的资源效率很高,但它在准确性、召回率、精度和F1分数方面的结果与其他基线模型相当。本文章由计算机程序翻译,如有差异,请以英文原文为准。
Lightweight representation learning for network traffic towards malicious traffic detection in edge devices
With the rapid increase in the number of connected devices in the Internet of Things (IoT) environment, their exposure to threats has increased significantly. The attackers can launch sophisticated attacks on these networks more frequently due to the ease of availability of computing facilities. The devices in the IoT network have limited computational power, storage capacity, and hardware capability, making it challenging to secure them using traditional approaches. Over the years, many machine learning and deep learning-based approaches have been proposed to classify the traffic flowing through the edge devices, but the models have their limitations, such as slow detection of the attacks because of the limited computational power of these devices, thereby rendering parameter-heavy models infeasible to be run on such devices. To overcome this, we propose a structure learning algorithm to create a model whose structure learning is done using correlation analysis and PCA, then is optimized using parent divorcing and Sequential least squares programming, thereby creating a model that exhibits high performance despite being lean with respect to the number of parameters. The chosen features’ relevance for each attack is also validated via qualitative mapping and domain logic. The generated model, evaluated using UNSW-NB15 and TON-IoT datasets, outperformed several state-of-the-art models to classify malicious traffic, especially in terms of inference time and model size. Despite its resource efficiency, it shows comparable results in terms of accuracy, recall, precision, and F1 score with other baseline models.
求助全文
通过发布文献求助,成功后即可免费获取论文全文。
去求助
来源期刊

Journal of Information Security and Applications
Computer Science-Computer Networks and Communications
CiteScore
10.90
自引率
5.40%
发文量
206
审稿时长
56 days
期刊介绍:
Journal of Information Security and Applications (JISA) focuses on the original research and practice-driven applications with relevance to information security and applications. JISA provides a common linkage between a vibrant scientific and research community and industry professionals by offering a clear view on modern problems and challenges in information security, as well as identifying promising scientific and "best-practice" solutions. JISA issues offer a balance between original research work and innovative industrial approaches by internationally renowned information security experts and researchers.
 求助内容:
求助内容: 应助结果提醒方式:
应助结果提醒方式:


