提高汽车网络安全性的多域欺骗
IF 5.4
2区 计算机科学
Q1 COMPUTER SCIENCE, INFORMATION SYSTEMS
引用次数: 0
摘要
随着汽车行业越来越多地整合数字技术,网络攻击的威胁已成为一个关键问题。在这项工作中,我们提出了两种不同的网络欺骗策略:反应性欺骗,它利用多域架构来减轻远程攻击,以及主动欺骗,专注于蜜罐的战略分配。响应式方法通过实施相互依赖的欺骗框架来解决互联汽车系统中的协调和同步挑战,从而增强对多方面网络威胁的保护。相比之下,主动策略采用多目标优化框架有效分配蜜罐,获得平衡竞争防御目标的帕累托纳什均衡解。我们定量地比较了我们的多域反应方法与传统的单域策略,在复杂的跨域攻击场景中展示了显著的防御优势。实验结果表明,与传统方法相比,多域策略的防御效能提高了约19%。本文章由计算机程序翻译,如有差异,请以英文原文为准。
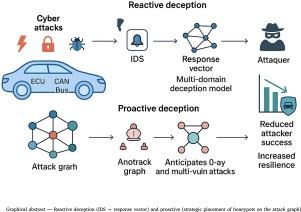
Multi-domain deception for enhanced security in automotive networks
As the automotive industry increasingly integrates digital technologies, the threat of cyberattacks has emerged as a critical concern. In this work, we propose two distinct cyber deception strategies: reactive deception, which leverages multi-domain architectures to mitigate remote attacks, and proactive deception, focused on the strategic allocation of honeypots. The reactive approach addresses coordination and synchronization challenges in interconnected automotive systems by implementing an interdependent deception framework, thereby enhancing protection against multi-faceted cyber threats. In contrast, the proactive strategy employs a multi-objective optimization framework to allocate honeypots effectively, achieving Pareto Nash equilibrium solutions that balance competing defense objectives. We quantitatively compare our multi-domain reactive approach with traditional single-domain strategies, demonstrating significant defensive advantages in complex, cross-domain attack scenarios. Experimental results reveal that the multi-domain strategy improves defense effectiveness by approximately 19% compared to conventional methods.
求助全文
通过发布文献求助,成功后即可免费获取论文全文。
去求助
来源期刊

Computers & Security
工程技术-计算机:信息系统
CiteScore
12.40
自引率
7.10%
发文量
365
审稿时长
10.7 months
期刊介绍:
Computers & Security is the most respected technical journal in the IT security field. With its high-profile editorial board and informative regular features and columns, the journal is essential reading for IT security professionals around the world.
Computers & Security provides you with a unique blend of leading edge research and sound practical management advice. It is aimed at the professional involved with computer security, audit, control and data integrity in all sectors - industry, commerce and academia. Recognized worldwide as THE primary source of reference for applied research and technical expertise it is your first step to fully secure systems.
 求助内容:
求助内容: 应助结果提醒方式:
应助结果提醒方式:


