率先使用 KEVM 对区块链中的智能合约进行自动漏洞检测:守护者 ADRGAN
摘要
智能合约的功能类似于区块链上的专用计算机程序。以太坊上有许多这样的合约,但有时这些合约会出现安全问题。这些问题造成了巨大的资金损失,并降低了区块链的稳定性。智能合约是具有预定义规则的自执行合约,是许多区块链应用的核心。但是,它们容易受到各种漏洞和安全风险的影响。自动漏洞检测有助于有效识别和缓解这些问题。智能合约(SC)最近非常流行。人们认为它们是在区块链上进行交易的未来。智能合约就像自动协议。它们使用特殊的计算机程序自行运行。它们遵循交易规则并跟踪一切。智能合约的主要理念是摆脱对传统的可信中间人(如权威机构或组织)的需求。相反,我们使用在安全且不可更改的系统上运行的代码。在本手稿中,我们将使用 KEVM 对区块链中的智能合约进行自动漏洞检测:Guardian ADRGAN(ADRGAN-SCB-KEVM)。在这里,K 框架的以太坊虚拟机(KEVM)是本研究中使用的计算引擎。通过 KEVM,智能合约数据被提供给特征提取阶段。特征提取采用基于嵌套补丁的特征提取方法。然后,将提取的特征输送到entive dual residual generative adversarial network (ADRGAN),识别 KEVM 智能合约的漏洞。最后,使用 ADRGAN 将智能合约分为易受攻击(Vulnerable)和非易受攻击(Non-Vulnerable)两类。所提出的 ADRGAN-SCB-KEVM 方法在 Python 上使用,并通过不同的指标(如准确率、计算时间、精确度、召回率、F1 分数、特异性、RoC)对所提出方法的效率进行了评估。模拟结果证明,所提出的 ADRGAN-SCB-KEVM 技术对于易受攻击目标的准确率分别提高了 41.34%、31.28% 和 36.38%;对于非易受攻击目标的准确率分别提高了 32.44%、38.45% 和 29.47%。与现有方法相比,如利用故障注入评估存在故障智能合约的区块链系统(UFI-BS-ESVD)、高校区块链智能合约应用现状(SA-BESC-ESVD)、通过计算以太坊字节码的精确控制流图增强以太坊智能合约静态分析(EESC-CPC-EBD)等,非漏洞的准确率分别提高了 32.44%、38.45% 和 29.47%。
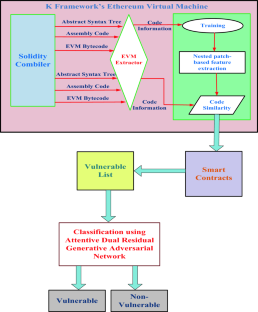
Smart contracts function like specialized computer programs on the blockchain. Many of these contracts are on Ethereum, but sometimes these contracts have problems with security. These problems caused big money losses and made the blockchain less stable. Smart contracts are self-executing with predefined rules and are at the core of many blockchain applications. However, they are susceptible to various vulnerabilities and security risks. Automated vulnerability detection helps identify and mitigate these issues efficiently. Smart Contracts (SC) have become really popular lately. People think they are the future for making deals on blockchains. Smart contracts are like automatic agreements. They work by themselves using special computer programs. They follow the rules of the deal and keep track of everything. The main idea with smart contracts is to get rid of the need for traditional trusted middlemen-like authorities or organizations. Instead, we use code that runs on a secure and unchangeable system. In this manuscript, pioneering automated vulnerability detection for smart contracts in blockchain using KEVM: Guardian ADRGAN (ADRGAN-SCB-KEVM) is proposed. Here, K framework’s Ethereum virtual machine (KEVM) is a computation engine used in this research. From this KEVM, smart contracts data are provided to feature extraction phase. Feature extraction is done using Nested patch-based feature extraction. Then the extracted features are fed to attentive dual residual generative adversarial network (ADRGAN), identifying KEVM smart contracts vulnerabilities. Finally, by using ADRGAN, it is classified as Vulnerable and Non-Vulnerable in smart contracts. The proposed ADRGAN-SCB-KEVM method employed on Python and efficiency of proposed method evaluated with different metrics like Accuracy, Computation Time, Precision, Recall, F1 Score, Specificity, RoC are evaluated. The simulation outcomes prove that the proposed ADRGAN-SCB-KEVM technique attains 41.34%, 31.28%, and 36.38% higher Accuracy for Vulnerable; 32.44%, 38.45%, and 29.47% higher Accuracy for Non-Vulnerable while compared with the existing methods such as Utilizing fault injection to evaluate blockchain systems in the presence of faulty smart contracts (UFI-BS-ESVD), State-of-the-Art Blockchain-Enabled Smart Contract Applications in the University (SA-BESC-ESVD), enhancing Ethereum smart contracts static analysis by computing precise Control-Flow Graph of Ethereum bytecode (EESC-CPC-EBD), respectively.

 求助内容:
求助内容: 应助结果提醒方式:
应助结果提醒方式:


