在买家和卖家的异构网络中检测虚假评论者:一种基于协作训练的垃圾邮件发送者群体算法
IF 3.9
4区 计算机科学
Q2 COMPUTER SCIENCE, INFORMATION SYSTEMS
引用次数: 0
摘要
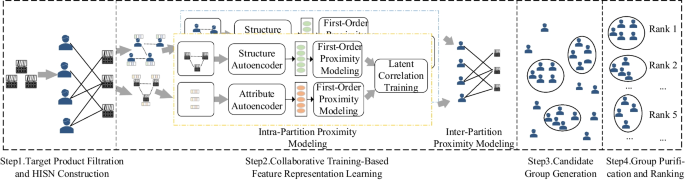
恶意卖家与虚假评论者(也称为垃圾邮件制造者)串通为多个产品撰写虚假评论,以贬低竞争对手或提升其产品声誉,形成灰色产业链的现象并不少见。为了在具有丰富的买卖双方语义信息的异构网络中检测垃圾邮件发送者群体,研究人员使用基于频繁项挖掘和基于图的方法进行了广泛的研究。但是,这些方法不能检测跨产品攻击的垃圾邮件发送者组,没有联合考虑结构和属性特征以及结构-属性相关性,导致检测性能较差。因此,我们提出了一种基于协同训练的垃圾邮件组检测算法,该算法基于目标产品集构建异构诱导子网络来检测跨产品攻击的垃圾邮件组。为了共同考虑所有可用的特征,我们使用协同训练方法来学习节点的特征表示。此外,我们使用DBSCAN聚类方法生成候选组,排除无害组,并对它们进行排序以获得垃圾邮件发送者组。在真实数据集上的实验结果表明,该方法的整体检测性能优于基线方法。本文章由计算机程序翻译,如有差异,请以英文原文为准。
Detecting fake reviewers in heterogeneous networks of buyers and sellers: a collaborative training-based spammer group algorithm
Abstract It is not uncommon for malicious sellers to collude with fake reviewers (also called spammers) to write fake reviews for multiple products to either demote competitors or promote their products’ reputations, forming a gray industry chain. To detect spammer groups in a heterogeneous network with rich semantic information from both buyers and sellers, researchers have conducted extensive research using Frequent Item Mining-based and graph-based methods. However, these methods cannot detect spammer groups with cross-product attacks and do not jointly consider structural and attribute features, and structure-attribute correlation, resulting in poorer detection performance. Therefore, we propose a collaborative training-based spammer group detection algorithm by constructing a heterogeneous induced sub-network based on the target product set to detect cross-product attack spammer groups. To jointly consider all available features, we use the collaborative training method to learn the feature representations of nodes. In addition, we use the DBSCAN clustering method to generate candidate groups, exclude innocent ones, and rank them to obtain spammer groups. The experimental results on real-world datasets indicate that the overall detection performance of the proposed method is better than that of the baseline methods.
求助全文
通过发布文献求助,成功后即可免费获取论文全文。
去求助
来源期刊

Cybersecurity
Computer Science-Information Systems
CiteScore
7.30
自引率
0.00%
发文量
77
审稿时长
9 weeks
 求助内容:
求助内容: 应助结果提醒方式:
应助结果提醒方式:


