Ransomware dynamics: Mitigating personal data exfiltration through the SCIRAS lens
IF 5.4
2区 计算机科学
Q1 COMPUTER SCIENCE, INFORMATION SYSTEMS
引用次数: 0
Abstract
Ransomware’s capability to exfiltrate personal data is one of the most significant threats to privacy today. Its growing complexity and resistance to static analysis have driven research efforts to implement security controls on endpoints using dynamic analysis. However, the critical security threshold that these endpoint controls must overcome to effectively mitigate personal data exfiltration and stop ransomware propagation once an infection has begun in communication networks remains unclear. This paper addresses this issue by analyzing the Susceptible–Carriers–Infected–Recovered–Attacked–Susceptible (SCIRAS) epidemiological model in the context of a critical ransomware attack, with limited network and administrative security, that defines the critical scenario to be overcome. Unlike previous studies, this research first estimates a critical execution rate by studying the behavior of LockBit, Ryuk, and TeslaCrypt ransomware families and simulating CL0P MOVEit and Conti attacks in a controlled environment. To reflect more realistic conditions, we introduce a critical dynamic infection rate based on the critical execution rate, several attack vectors of modern ransomware, and the effect of limited network security. Using this baseline, a proposed triple extortion SCIRAS model is simulated and analyzed under its estimated parameters’ critical values to solve for each ransomware family the optimization problem of finding the critical security threshold required for endpoint controls to reach the Kermack and McKendrick’s non-epidemic status with the minimum feasible basic reproduction number. Our results demonstrate that a critical security threshold of at least 0.961 might contain modern ransomware exceeding the thresholds reported in previous simulations of SCIRAS and other models. Furthermore, we introduce a novel deep-learning-based framework called RansomSentinel, validated on the RanSAP120GB, RanSAP250GB, and RanSMAP datasets, which outperforms traditional machine learning classifiers and surpasses the estimated critical security threshold of each analyzed ransomware family.
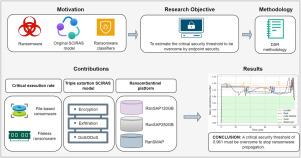
勒索软件动态:通过SCIRAS镜头减轻个人数据泄露
勒索软件窃取个人数据的能力是当今对隐私最严重的威胁之一。其日益增长的复杂性和对静态分析的抵制促使研究人员努力使用动态分析在端点上实现安全控制。然而,这些端点控制必须克服的关键安全阈值,才能有效地减轻个人数据泄露,并在通信网络感染开始后阻止勒索软件的传播,目前尚不清楚。本文通过分析关键勒索软件攻击背景下的易感-携带者-感染-恢复-攻击-易感(SCIRAS)流行病学模型来解决这个问题,该模型具有有限的网络和管理安全性,定义了要克服的关键场景。与之前的研究不同,本研究首先通过研究LockBit、Ryuk和TeslaCrypt勒索软件家族的行为,并在受控环境中模拟CL0P MOVEit和Conti攻击来估计临界执行速率。为了反映更现实的情况,我们基于临界执行速率、现代勒索软件的几种攻击向量以及有限网络安全的影响引入了临界动态感染率。利用该基线,对所提出的三重勒索SCIRAS模型在其估计参数的临界值下进行了仿真分析,解决了每个勒索软件家族寻找端点控制以最小可行基本复制数达到Kermack和McKendrick非流行状态所需的临界安全阈值的优化问题。我们的研究结果表明,至少0.961的关键安全阈值可能包含超过先前SCIRAS和其他模型模拟中报告的阈值的现代勒索软件。此外,我们引入了一种新的基于深度学习的框架,称为RansomSentinel,在RanSAP120GB, RanSAP250GB和RanSMAP数据集上进行了验证,该框架优于传统的机器学习分类器,并超过了每个分析勒索软件家族的估计关键安全阈值。
本文章由计算机程序翻译,如有差异,请以英文原文为准。
求助全文
约1分钟内获得全文
求助全文
来源期刊

Computers & Security
工程技术-计算机:信息系统
CiteScore
12.40
自引率
7.10%
发文量
365
审稿时长
10.7 months
期刊介绍:
Computers & Security is the most respected technical journal in the IT security field. With its high-profile editorial board and informative regular features and columns, the journal is essential reading for IT security professionals around the world.
Computers & Security provides you with a unique blend of leading edge research and sound practical management advice. It is aimed at the professional involved with computer security, audit, control and data integrity in all sectors - industry, commerce and academia. Recognized worldwide as THE primary source of reference for applied research and technical expertise it is your first step to fully secure systems.
 求助内容:
求助内容: 应助结果提醒方式:
应助结果提醒方式:


