Lightweight privacy-preserving authenticated key agreements using physically unclonable functions for internet of drones
IF 3.8
2区 计算机科学
Q2 COMPUTER SCIENCE, INFORMATION SYSTEMS
Journal of Information Security and Applications
Pub Date : 2024-11-15
DOI:10.1016/j.jisa.2024.103915
引用次数: 0
Abstract
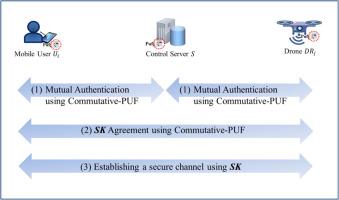
The Internet of Drones (IoD) means the cooperative collection and transmission of data by multiple drones in a cluster or decentralized way of working to decrease the energy consumption of mobile devices, increase overall performance, and reduce the cost of building infrastructure. It is widely applied in various fields, including environmental scouting and monitoring, emergency assistance and logistics transportation, etc. Recently, many related authentication schemes were proposed for IoD. Due to the limitation that the drones use lightweight components for development, these authentication schemes mostly use lightweight components for development. However, many authentication schemes cannot overcome security issues such as providing user privacy protection and resisting drone capture attacks. This study discusses these security issues of related schemes, and develops an authentication scheme for IoD by using Physically Unclonable Functions (PUF). Due to its own microscopic characteristics, the PUF can generate unpredictable and duplicate information, which can be regarded as a device fingerprint and is suitable for device authentication. Additionally, this study utilizes the commutative and invertible properties of BS-PUF to develop the key exchange of the proposed scheme and to protect user privacy. This proposed scheme overcomes the previous problems in security, has more security features, and maintains lightweight computational costs.
为无人机互联网使用物理不可克隆函数的轻量级隐私保护认证密钥协议
无人机互联网(IoD)是指多架无人机以集群或分散的工作方式合作收集和传输数据,从而降低移动设备的能耗,提高整体性能,降低基础设施建设成本。它被广泛应用于各个领域,包括环境侦察和监测、紧急援助和物流运输等。最近,许多相关的身份验证方案被提出用于物联网。由于无人机使用轻量级组件进行开发的局限性,这些认证方案大多使用轻量级组件进行开发。然而,许多身份验证方案无法克服安全问题,如提供用户隐私保护和抵御无人机捕获攻击。本研究讨论了相关方案的这些安全问题,并利用物理不可克隆函数(PUF)开发了一种用于 IoD 的身份验证方案。由于 PUF 自身的微观特性,它可以生成不可预测的重复信息,可视为设备指纹,适用于设备身份验证。此外,本研究还利用了 BS-PUF 的交换和可逆特性来开发拟议方案的密钥交换,并保护用户隐私。该方案克服了以往在安全性方面存在的问题,具有更多的安全特性,并保持了轻量级计算成本。
本文章由计算机程序翻译,如有差异,请以英文原文为准。
求助全文
约1分钟内获得全文
求助全文
来源期刊

Journal of Information Security and Applications
Computer Science-Computer Networks and Communications
CiteScore
10.90
自引率
5.40%
发文量
206
审稿时长
56 days
期刊介绍:
Journal of Information Security and Applications (JISA) focuses on the original research and practice-driven applications with relevance to information security and applications. JISA provides a common linkage between a vibrant scientific and research community and industry professionals by offering a clear view on modern problems and challenges in information security, as well as identifying promising scientific and "best-practice" solutions. JISA issues offer a balance between original research work and innovative industrial approaches by internationally renowned information security experts and researchers.
 求助内容:
求助内容: 应助结果提醒方式:
应助结果提醒方式:


