How to assess measurement capabilities of a security monitoring infrastructure and plan investment through a graph-based approach
IF 7.5
1区 计算机科学
Q1 COMPUTER SCIENCE, ARTIFICIAL INTELLIGENCE
引用次数: 0
Abstract
Security monitoring is a crucial activity in managing cybersecurity for any organization, as it plays a foundational role in various security processes and systems, such as risk identification and threat detection. To be effective, security monitoring is currently implemented by orchestrating multiple data sources to provide corrective actions promptly. Poor monitoring management can compromise an organization’s cybersecurity posture and waste resources. This issue is further exacerbated by the fact that monitoring infrastructures are typically managed with a limited resource budget. This paper addresses the problem of supporting security experts in managing security infrastructures efficiently and effectively by considering the trade-off cost-benefit between using specific monitoring tools and the benefit of including them in the organization’s infrastructure. To this aim, we introduce a graph-based model named Metric Graph Model (MGM) to represent dependencies between security metrics and the monitoring infrastructure. It is used to solve a set of security monitoring problems: (i) Metrics Computability, to assess the measurement capabilities of the monitoring infrastructure, (ii) Instrument Redundancy, to assess the utility of the instruments used for the monitoring, and (iii) Cost-Bounded Constraint, to identify the optimal monitoring infrastructure in terms of cost-benefit trade-off. We prove the NP-hardness of some of these problems, propose heuristics for solving them based on the Metric Graph Model and provide an experimental evaluation that shows their better performance than existing solutions. Finally, we present a usage scenario based on an instance of the Metric Graph Model derived from a state-of-the-art security metric taxonomy currently employed by organizations. It demonstrates how the proposed approach supports an administrator in optimizing the security monitoring infrastructure in terms of saving resources and speeding up the decision-making process.
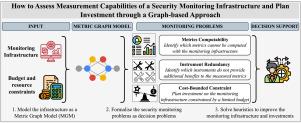
如何通过基于图表的方法评估安全监控基础设施的测量能力并规划投资
安全监控是任何组织管理网络安全的关键活动,因为它在风险识别和威胁检测等各种安全流程和系统中发挥着基础性作用。目前,安全监控是通过协调多个数据源来实施的,以便及时提供纠正措施。监控管理不善会损害组织的网络安全态势并浪费资源。由于监控基础设施的管理资源预算通常有限,这一问题进一步加剧。本文通过考虑使用特定监控工具的成本效益权衡,以及将这些工具纳入组织基础设施的好处,来解决支持安全专家高效管理安全基础设施的问题。为此,我们引入了一个基于图的模型,名为 "度量图模型"(MGM),用于表示安全度量和监控基础设施之间的依赖关系。该模型用于解决一系列安全监控问题:(i) 指标可计算性,用于评估监控基础设施的测量能力;(ii) 仪器冗余,用于评估监控所用仪器的效用;以及 (iii) 成本约束,用于确定成本效益权衡方面的最佳监控基础设施。我们证明了其中一些问题的 NP 难度,提出了基于度量图模型解决这些问题的启发式方法,并进行了实验评估,结果表明其性能优于现有解决方案。最后,我们介绍了一个基于公制图模型实例的使用场景,该实例源于企业目前采用的最先进的安全指标分类法。它展示了所提出的方法如何在节省资源和加快决策过程方面支持管理员优化安全监控基础设施。
本文章由计算机程序翻译,如有差异,请以英文原文为准。
求助全文
约1分钟内获得全文
求助全文
来源期刊

Expert Systems with Applications
工程技术-工程:电子与电气
CiteScore
13.80
自引率
10.60%
发文量
2045
审稿时长
8.7 months
期刊介绍:
Expert Systems With Applications is an international journal dedicated to the exchange of information on expert and intelligent systems used globally in industry, government, and universities. The journal emphasizes original papers covering the design, development, testing, implementation, and management of these systems, offering practical guidelines. It spans various sectors such as finance, engineering, marketing, law, project management, information management, medicine, and more. The journal also welcomes papers on multi-agent systems, knowledge management, neural networks, knowledge discovery, data mining, and other related areas, excluding applications to military/defense systems.
 求助内容:
求助内容: 应助结果提醒方式:
应助结果提醒方式:


