Who is vulnerable to deceptive design patterns? A transdisciplinary perspective on the multi-dimensional nature of digital vulnerability
IF 3.2
3区 社会学
Q1 LAW
引用次数: 0
Abstract
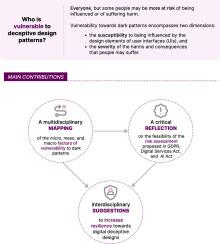
In the last few years, there have been growing concerns about the far-reaching influence that digital architectures may exert on individuals and societies. A specific type of digital manipulation is often engineered into the interfaces of digital services through the use of so-called dark patterns, that cause manifold harms against which nobody seems to be immune. However, many areas of law rely on a traditional class-based view according to which certain groups are inherently more vulnerable than others, such as children. Although the undue influence exerted by dark patterns on online decisions can befall anybody, empirical studies show that there are actually certain factors that aggravate the vulnerability of some people by making them more likely to incur in certain manipulation risks engineered in digital services and less resilient to the related harms. But digital vulnerability does not overlap with traditionally protected groups and depends on multifaceted factors. This article contributes to the ongoing discussions on these topics by offering (i) a multidisciplinary mapping of the micro, meso, and macro factors of vulnerability to dark patterns; (ii) a subsequent critical reflection on the feasibility of the risk assessment proposed in three selected EU legal frameworks: the General Data Protection Regulation, the Digital Services Act, and the Artificial Intelligence Act; (iii) and multidisciplinary suggestions to increase resilience towards manipulative designs online.
谁容易受到欺骗性设计模式的影响?从跨学科角度看数字脆弱性的多面性
最近几年,人们越来越关注数字架构可能对个人和社会产生的深远影响。一种特殊的数字操纵往往通过使用所谓的 "黑暗模式"(dark pattern)被设计到数字服务的界面中,造成多方面的伤害,似乎没有人能够幸免。然而,许多法律领域依赖于传统的阶级观点,根据这种观点,某些群体天生就比其他群体更容易受到伤害,比如儿童。尽管黑暗模式对在线决策的不当影响可能会降临到任何人身上,但实证研究表明,实际上有某些因素加剧了某些人的脆弱性,使他们更有可能遭受数字服务中的某些操纵风险,对相关危害的抵御能力也更弱。但数字脆弱性与传统上受保护的群体并不重叠,而是取决于多方面的因素。本文通过提供:(i) 易受黑暗模式影响的微观、中观和宏观因素的多学科图谱;(ii) 随后对三个选定的欧盟法律框架(《通用数据保护条例》、《数字服务法》和《人工智能法》)中提出的风险评估的可行性进行批判性反思;(iii) 以及提高对在线操纵设计的抵御能力的多学科建议,为正在进行的有关这些主题的讨论做出贡献。
本文章由计算机程序翻译,如有差异,请以英文原文为准。
求助全文
约1分钟内获得全文
求助全文
来源期刊
CiteScore
5.60
自引率
10.30%
发文量
81
审稿时长
67 days
期刊介绍:
CLSR publishes refereed academic and practitioner papers on topics such as Web 2.0, IT security, Identity management, ID cards, RFID, interference with privacy, Internet law, telecoms regulation, online broadcasting, intellectual property, software law, e-commerce, outsourcing, data protection, EU policy, freedom of information, computer security and many other topics. In addition it provides a regular update on European Union developments, national news from more than 20 jurisdictions in both Europe and the Pacific Rim. It is looking for papers within the subject area that display good quality legal analysis and new lines of legal thought or policy development that go beyond mere description of the subject area, however accurate that may be.

 求助内容:
求助内容: 应助结果提醒方式:
应助结果提醒方式:


