Development of novel intrusion detection in Internet of Things using improved dart game optimizer-derived optimal cascaded ensemble learning
Abstract
Background of the Study
Internet of things (IoT) industry has accelerated its development with the support of advanced information technology and economic expansion. A complete industrial foundation includes software, chips, electronic components, IoT services, integrated systems, machinery, and telecom operators, which the gradual improvement in the IoT industry system has formulated. As the exponential growth of IoT devices increases, the attack surface available to cybercriminals enables them to carry out potentially more damaging operations. As a result, the security sector has witnessed a rise in cyberattacks. Hackers use several methods to copy and modify the information in the IoT environment. Machine learning techniques are used by the intrusion detection (ID) model to determine and categorize attacks in IoT networks.
Objectives
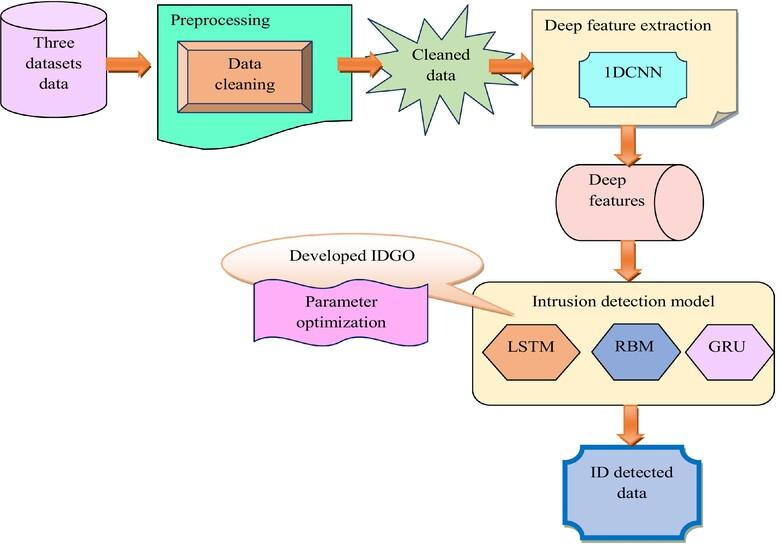
Thus, this study explores the ID system with the heuristic-assisted deep learning approaches for effectively detect the attacks in the IoT. At first, the IoT data are garnered in benchmark resources. Then, the gathered data is preprocessed to perform data cleaning. Next, the data is transformed and fed to the feature extraction stage. The feature extraction is performed with the help of one-dimensional convolutional neural network (1D-CNN), where the features are extracted from the target-based pooling layer. Then, these attained deep features are fed to the ID phase, where the cascaded ensemble learning (CEL) approach is adopted for detecting the intrusions. Here, the hyperparameter tuning is done with a new suggested improved darts game optimizer (IDGO) algorithm. Here, the main objective of the developed algorithm helps to maximize accuracy in ID.
Findings
Throughout the experimental findings, the developed model provides 86% of accuracy. Thus, the finding of the developed model shows less detecting time and higher detection efficiency.

 求助内容:
求助内容: 应助结果提醒方式:
应助结果提醒方式:


