Learning autoencoder ensembles for detecting malware hidden communications in IoT ecosystems
IF 3.4
3区 计算机科学
Q3 COMPUTER SCIENCE, ARTIFICIAL INTELLIGENCE
引用次数: 0
Abstract
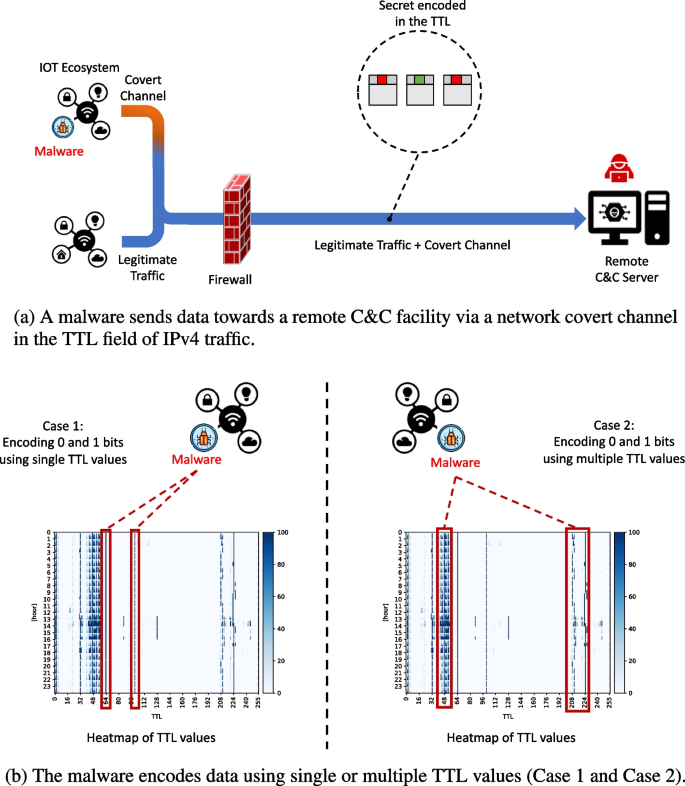
Abstract Modern IoT ecosystems are the preferred target of threat actors wanting to incorporate resource-constrained devices within a botnet or leak sensitive information. A major research effort is then devoted to create countermeasures for mitigating attacks, for instance, hardware-level verification mechanisms or effective network intrusion detection frameworks. Unfortunately, advanced malware is often endowed with the ability of cloaking communications within network traffic, e.g., to orchestrate compromised IoT nodes or exfiltrate data without being noticed. Therefore, this paper showcases how different autoencoder-based architectures can spot the presence of malicious communications hidden in conversations, especially in the TTL of IPv4 traffic. To conduct tests, this work considers IoT traffic traces gathered in a real setting and the presence of an attacker deploying two hiding schemes (i.e., naive and “elusive” approaches). Collected results showcase the effectiveness of our method as well as the feasibility of deploying autoencoders in production-quality IoT settings.
学习自动编码器集成,用于检测物联网生态系统中的恶意软件隐藏通信
现代物联网生态系统是威胁行为者的首选目标,他们希望将资源受限的设备纳入僵尸网络或泄露敏感信息。然后,主要的研究工作致力于创建缓解攻击的对策,例如,硬件级验证机制或有效的网络入侵检测框架。不幸的是,高级恶意软件通常具有隐藏网络流量中的通信的能力,例如,编排受损的物联网节点或在不被发现的情况下泄露数据。因此,本文展示了不同的基于自动编码器的架构如何发现隐藏在会话中的恶意通信的存在,特别是在IPv4流量的TTL中。为了进行测试,这项工作考虑了在真实环境中收集的物联网流量痕迹以及部署两种隐藏方案(即幼稚和“难以捉摸”的方法)的攻击者的存在。收集的结果展示了我们方法的有效性,以及在生产质量的物联网设置中部署自动编码器的可行性。
本文章由计算机程序翻译,如有差异,请以英文原文为准。
求助全文
约1分钟内获得全文
求助全文
来源期刊

Journal of Intelligent Information Systems
工程技术-计算机:人工智能
CiteScore
7.20
自引率
11.80%
发文量
72
审稿时长
6-12 weeks
期刊介绍:
The mission of the Journal of Intelligent Information Systems: Integrating Artifical Intelligence and Database Technologies is to foster and present research and development results focused on the integration of artificial intelligence and database technologies to create next generation information systems - Intelligent Information Systems.
These new information systems embody knowledge that allows them to exhibit intelligent behavior, cooperate with users and other systems in problem solving, discovery, access, retrieval and manipulation of a wide variety of multimedia data and knowledge, and reason under uncertainty. Increasingly, knowledge-directed inference processes are being used to:
discover knowledge from large data collections,
provide cooperative support to users in complex query formulation and refinement,
access, retrieve, store and manage large collections of multimedia data and knowledge,
integrate information from multiple heterogeneous data and knowledge sources, and
reason about information under uncertain conditions.
Multimedia and hypermedia information systems now operate on a global scale over the Internet, and new tools and techniques are needed to manage these dynamic and evolving information spaces.
The Journal of Intelligent Information Systems provides a forum wherein academics, researchers and practitioners may publish high-quality, original and state-of-the-art papers describing theoretical aspects, systems architectures, analysis and design tools and techniques, and implementation experiences in intelligent information systems. The categories of papers published by JIIS include: research papers, invited papters, meetings, workshop and conference annoucements and reports, survey and tutorial articles, and book reviews. Short articles describing open problems or their solutions are also welcome.
 求助内容:
求助内容: 应助结果提醒方式:
应助结果提醒方式:


