Blockchain-based biometric identity management
IF 4.1
3区 计算机科学
Q2 COMPUTER SCIENCE, INFORMATION SYSTEMS
Cluster Computing-The Journal of Networks Software Tools and Applications
Pub Date : 2023-11-07
DOI:10.1007/s10586-023-04180-x
引用次数: 0
Abstract
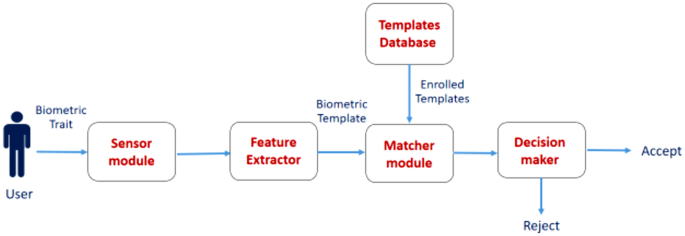
Abstract In recent years, face biometrics recognition systems are a wide space of a computer usage which is mostly employed for security purpose. The main purpose of the face biometrics recognition system is to authenticate a user from a given database. Due to the widespread expansion of the surveillance cameras and facial recognition technology, a robust face recognition system required. The recognition system needs to store a large number of training samples in any storage unit, that time hackers can access and control that data. So, Protecting and managing sensitive data is essential object. This requires a technique that preserve the privacy of individuals, maintain data integrity, and prevent information leakage. The storage of biometric templates on centralized servers has been associated with potential privacy risks. To address this issue, we have developed and implemented a proof-of-concept facial biometric identification system that uses a private Blockchain platform and smart contract technology. So, the proposed approach is presented a secure and tamper-proof from data breaches as well as hacks with data availability, by using the Blockchain platform to store face images. This paper aims to utilize Blockchain technology to identify individuals based on their biometric traits, specifically facial recognition system makes it tamper-proof (immutable) ensuring security. The system consists of enrolment and authentication phases. Blockchain technology uses peer-to-peer communication, cryptography, consensus processes, and smart contracts to ensure the security. The proposed approach was tested on two popular datasets: CelebFaces Attributes (CelebA) and large-scale face UTKFace datasets. The experimental results indicate that the system yields highly performance outcomes, as evidenced by the Equal Error Rate (EER) values of 0.05% and 0.07% obtained for the CelebA and UTKFace datasets, respectively. The system was compared to three baseline methods and scored the lowest Equal Error Rate.
基于区块链的生物识别身份管理
摘要:人脸生物识别系统是近年来计算机应用的一个广泛领域,主要用于安全目的。人脸生物识别系统的主要目的是从给定的数据库中对用户进行身份验证。随着监控摄像机和人脸识别技术的广泛应用,需要一个强大的人脸识别系统。识别系统需要在任何存储单元中存储大量的训练样本,这样黑客就可以访问和控制这些数据。因此,保护和管理敏感数据是必不可少的目标。这需要一种保护个人隐私、维护数据完整性和防止信息泄露的技术。在集中式服务器上存储生物识别模板会带来潜在的隐私风险。为了解决这个问题,我们开发并实施了一个概念验证面部生物识别系统,该系统使用私有区块链平台和智能合约技术。因此,通过使用区块链平台存储人脸图像,提出了一种安全和防篡改的方法,可以防止数据泄露以及数据可用性的黑客攻击。本文旨在利用区块链技术根据个人的生物特征识别个人,特别是面部识别系统使其防篡改(不可变),确保安全。该系统包括注册和认证两个阶段。区块链技术使用点对点通信、密码学、共识过程和智能合约来确保安全性。该方法在两个流行的数据集上进行了测试:CelebA和大规模人脸UTKFace数据集。实验结果表明,该系统产生了高性能的结果,CelebA和UTKFace数据集的等错误率(EER)分别为0.05%和0.07%。将该系统与三种基线方法进行比较,获得了最低的相等错误率。
本文章由计算机程序翻译,如有差异,请以英文原文为准。
求助全文
约1分钟内获得全文
求助全文
来源期刊
CiteScore
9.70
自引率
13.60%
发文量
298
审稿时长
3.0 months
期刊介绍:
Cluster Computing addresses the latest results in these fields that support High Performance Distributed Computing (HPDC). In HPDC environments, parallel and/or distributed computing techniques are applied to the solution of computationally intensive applications across networks of computers. The journal represents an important source of information for the growing number of researchers, developers and users of HPDC environments.
Cluster Computing: the Journal of Networks, Software Tools and Applications provides a forum for presenting the latest research and technology in the fields of parallel processing, distributed computing systems and computer networks.

 求助内容:
求助内容: 应助结果提醒方式:
应助结果提醒方式:


