Generic attacks on small-state stream cipher constructions in the multi-user setting
IF 3.9
4区 计算机科学
Q2 COMPUTER SCIENCE, INFORMATION SYSTEMS
引用次数: 0
Abstract
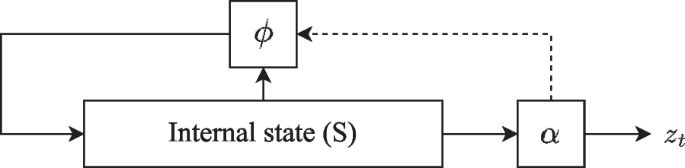
Abstract Small-state stream ciphers (SSCs), which violate the principle that the state size should exceed the key size by a factor of two, still demonstrate robust security properties while maintaining a lightweight design. These ciphers can be classified into several constructions and their basic security requirement is to resist generic attacks, i.e., the time–memory–data tradeoff (TMDTO) attack. In this paper, we investigate the security of small-state constructions in the multi-user setting. Based on it, the TMDTO distinguishing attack and the TMDTO key recovery attack are developed for such a setting. It is shown that SSCs which continuously use the key can not resist the TMDTO distinguishing attack. Moreover, SSCs based on the continuous-IV-key-use construction cannot withstand the TMDTO key recovery attack when the key length is shorter than the IV length, no matter whether the keystream length is limited or not. Finally, we apply these two generic attacks to TinyJAMBU and DRACO in the multi-user setting. The TMDTO distinguishing attack on TinyJAMBU with a 128-bit key can be mounted with time, memory, and data complexities of $$2^{64}$$
多用户环境下小状态流密码结构的通用攻击
小状态流密码(ssc)违反了状态大小应超过密钥大小两倍的原则,但在保持轻量级设计的同时仍具有强大的安全性。这些密码可以分为几种结构,它们的基本安全要求是抵抗通用攻击,即时间-内存-数据权衡(TMDTO)攻击。本文研究了多用户环境下小状态结构的安全性问题。在此基础上,开发了TMDTO识别攻击和TMDTO密钥恢复攻击。结果表明,连续使用该密钥的ssc无法抵抗TMDTO识别攻击。此外,无论是否限制密钥流长度,基于连续IV-key-use结构的ssc在密钥长度小于IV长度的情况下都无法抵御TMDTO密钥恢复攻击。最后,我们将这两种通用攻击应用于多用户环境下的《TinyJAMBU》和《DRACO》。使用128位密钥对TinyJAMBU进行TMDTO区分攻击时,时间、内存和数据复杂度分别为$$2^{64}$$ 2 64、$$2^{48}$$ 2 48和$$2^{32}$$ 2 32。这种攻击与ToSC 2022最近的工作相当,其中TinyJAMBU的部分密钥位被$$2^{50}$$ 250多个用户(或密钥)恢复。由于DRACO的IV长度小于其密钥长度,因此容易受到TMDTO密钥恢复攻击。由此产生的攻击具有$$2^{112}$$ 2 112的时间和内存复杂性,这意味着DRACO在多用户设置中不提供128位安全性。
本文章由计算机程序翻译,如有差异,请以英文原文为准。
求助全文
约1分钟内获得全文
求助全文
来源期刊

Cybersecurity
Computer Science-Information Systems
CiteScore
7.30
自引率
0.00%
发文量
77
审稿时长
9 weeks
 求助内容:
求助内容: 应助结果提醒方式:
应助结果提醒方式:


