An efficient permutation approach for SbPN-based symmetric block ciphers
IF 3.9
4区 计算机科学
Q2 COMPUTER SCIENCE, INFORMATION SYSTEMS
引用次数: 0
Abstract
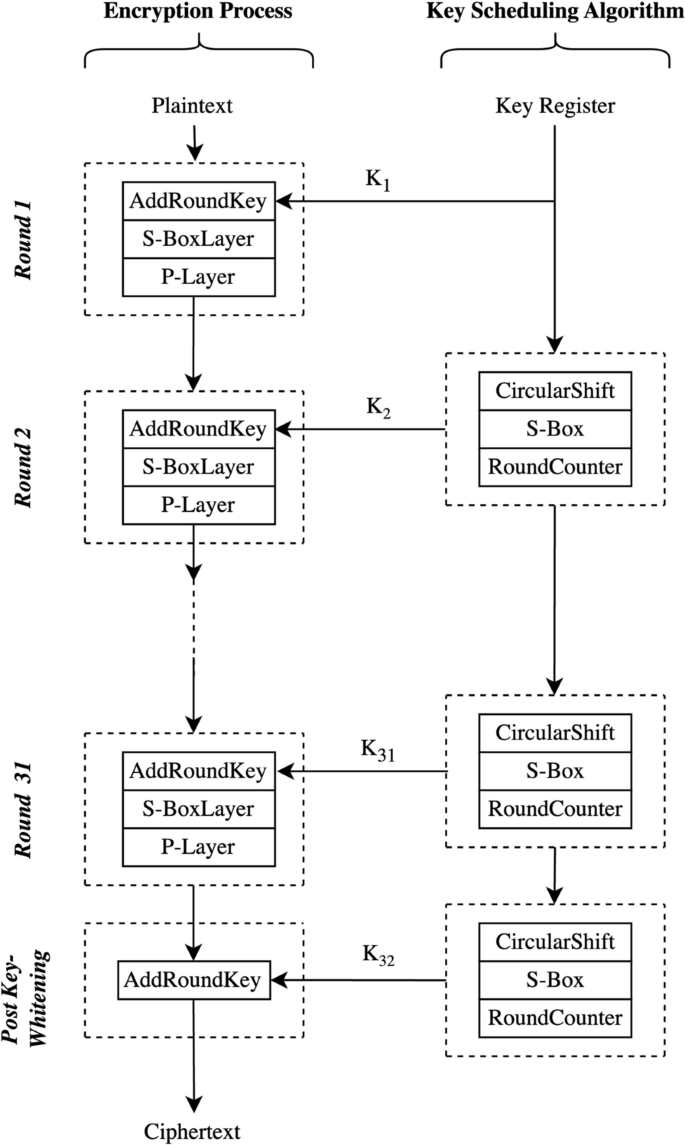
Abstract It is challenging to devise lightweight cryptographic primitives efficient in both hardware and software that can provide an optimum level of security to diverse Internet of Things applications running on low-end constrained devices. Therefore, an efficient hardware design approach that requires some specific hardware resource may not be efficient if implemented in software. Substitution bit Permutation Network based ciphers such as PRESENT and GIFT are efficient, lightweight cryptographic hardware design approaches. These ciphers introduce confusion and diffusion by employing a 4 × 4 static substitution box and bit permutations. The bit-wise permutation is realised by simple rerouting, which is most cost-effective to implement in hardware, resulting in negligible power consumption. However, this method is highly resource-consuming in software, particularly for large block-sized ciphers, with each single-bit permutation requiring multiple sub-operations. This paper proposes a novel software-based design approach for permutation operation in Substitution bit Permutation Network based ciphers using a bit-banding feature. The conventional permutation using bit rotation and the proposed approach have been implemented, analysed and compared for GIFT and PRESENT ciphers on ARM Cortex-M3-based LPC1768 development platform with KEIL MDK used as an Integrated Development Environment. The real-time performance comparison between conventional and the proposed approaches in terms of memory (RAM/ROM) footprint, power, energy and execution time has been carried out using ULINKpro and ULINKplus debug adapters for various code and speed optimisation scenarios. The proposed approach substantially reduces execution time, energy and power consumption for both PRESENT and GIFT ciphers, thus demonstrating the efficiency of the proposed method for Substitution bit Permutation Network based symmetric block ciphers.
基于sbpn的对称分组密码的一种高效排列方法
设计出在硬件和软件上都高效的轻量级加密原语,为运行在低端受限设备上的各种物联网应用程序提供最佳级别的安全性是一项挑战。因此,需要某些特定硬件资源的有效硬件设计方法如果在软件中实现可能并不有效。基于替换位置换网络的密码,如PRESENT和GIFT,是一种高效、轻量级的加密硬件设计方法。这些密码通过使用4 × 4静态替换盒和位置换引入混淆和扩散。通过简单的重路由实现逐位排列,这在硬件中实现是最经济有效的,导致功耗可以忽略不计。然而,这种方法在软件中非常消耗资源,特别是对于大块大小的密码,每个单比特排列需要多个子操作。本文提出了一种利用位带特性的基于替换位置换网络的密码置换操作的软件设计方法。在基于ARM cortex - m3的LPC1768开发平台上,采用KEIL MDK作为集成开发环境,对GIFT和PRESENT密码进行了传统的位旋转置换和本文提出的方法的实现、分析和比较。使用ULINKpro和ULINKplus调试适配器进行各种代码和速度优化方案,在内存(RAM/ROM)占用、功率、能量和执行时间方面,对传统方法和提议方法进行了实时性能比较。所提出的方法大大减少了PRESENT和GIFT密码的执行时间、能量和功耗,从而证明了所提出的方法对于基于替换位置换网络的对称分组密码的效率。
本文章由计算机程序翻译,如有差异,请以英文原文为准。
求助全文
约1分钟内获得全文
求助全文
来源期刊

Cybersecurity
Computer Science-Information Systems
CiteScore
7.30
自引率
0.00%
发文量
77
审稿时长
9 weeks
 求助内容:
求助内容: 应助结果提醒方式:
应助结果提醒方式:


